Firts, thanks for your time.
I might say that it has not work for me yet.
I am gonna write here my build.prop:
begin common build properties
autogenerated by build/make/tools/buildinfo_common.sh
ro.system.build.date=Thu Feb 24 21:31:37 UTC 2022
ro.system.build.date.utc=1645738297
ro.system.build.fingerprint=OnePlus/OnePlus5/OnePlus5:10/QKQ1.191014.012/2010292059:user/release-keys
ro.system.build.id=RQ3A.211001.001
ro.system.build.tags=release-keys
ro.system.build.type=user
ro.system.build.version.incremental=eng.root.20220224.213248
ro.system.build.version.release=11
ro.system.build.version.release_or_codename=11
ro.system.build.version.sdk=30
ro.product.system.brand=OnePlus
ro.product.system.device=OnePlus5
ro.product.system.manufacturer=OnePlus
ro.product.system.model=ONEPLUS A5000
ro.product.system.name=OnePlus5
end common build properties
begin build properties
autogenerated by buildinfo.sh
ro.build.id=RQ3A.211001.001
ro.build.display.id=lineige_cheeseburger-user 11 RQ3A.211001.001 eng.root.20220224.213248 release-keys
ro.build.version.incremental=eng.root.20220224.213248
ro.build.version.sdk=30
ro.build.version.preview_sdk=0
ro.build.version.preview_sdk_fingerprint=REL
ro.build.version.codename=REL
ro.build.version.all_codenames=REL
ro.build.version.release=11
ro.build.version.release_or_codename=11
ro.build.version.security_patch=2022-01-05
ro.eos.version.security_patch=
ro.build.version.base_os=
ro.build.version.min_supported_target_sdk=23
ro.build.date=Thu Feb 24 21:31:37 UTC 2022
ro.build.date.utc=1645738297
ro.build.type=user
ro.build.user=root
ro.build.host=runner-j3uhvwmz-project-53-concurrent-0
ro.build.tags=release-keys
ro.build.flavor=lineige_cheeseburger-user
ro.product.cpu.abi and ro.product.cpu.abi2 are obsolete,
use ro.product.cpu.abilist instead.
ro.product.cpu.abi=arm64-v8a
ro.product.cpu.abilist=arm64-v8a,armeabi-v7a,armeabi
ro.product.cpu.abilist32=armeabi-v7a,armeabi
ro.product.cpu.abilist64=arm64-v8a
ro.product.locale=en-US
ro.wifi.channels=
ro.build.product is obsolete; use ro.product.device
ro.build.product=cheeseburger
Do not try to parse description or thumbprint
ro.build.description=OnePlus5-user 10 QKQ1.191014.012 2010292059 release-keys
ro.lineige.device=cheeseburger
end build properties
from device/oneplus/msm8998-common/system.prop
Audio
af.fast_track_multiplier=1
audio.deep_buffer.media=true
audio.offload.min.duration.secs=30
audio.offload.video=true
ro.af.client_heap_size_kbyte=7168
ro.config.media_vol_steps=25
ro.config.vc_call_vol_steps=6
Camera
camera.disable_zsl_mode=1
Charger
ro.charger.disable_init_blank=true
ro.charger.enable_suspend=true
DRM
drm.service.enabled=true
FRP
ro.frp.pst=/dev/block/bootdevice/by-name/config
Graphics
debug.gralloc.enable_fb_ubwc=1
debug.sf.disable_backpressure=1
debug.sf.enable_hwc_vds=1
debug.sf.hw=1
debug.sf.latch_unsignaled=1
dev.pm.dyn_samplingrate=1
persist.demo.hdmirotationlock=false
persist.hwc.enable_vds=1
persist.sys.wfd.virtual=0
ro.opengles.version=196610
Media
media.stagefright.thumbnail.prefer_hw_codecs=true
vidc.enc.dcvs.extra-buff-count=2
OEM Unlock
ro.oem_unlock_supported=1
RIL
keyguard.no_require_sim=true
persist.radio.multisim.config=dsds
ril.subscription.types=NV,RUIM
ro.com.android.dataroaming=true
ro.telephony.call_ring.multiple=false
ro.telephony.default_network=22,20
ro.telephony.iwlan_operation_mode=legacy
telephony.lteOnCdmaDevice=1
SurfaceFlinger
ro.surface_flinger.force_hwc_copy_for_virtual_displays=true
ro.surface_flinger.max_frame_buffer_acquired_buffers=3
ro.surface_flinger.max_virtual_display_dimension=4096
ro.surface_flinger.protected_contents=true
TimeService
persist.timed.enable=true
VoLTE
persist.dbg.volte_avail_ovr=1
persist.dbg.vt_avail_ovr=1
persist.dbg.wfc_avail_ovr=1
Wi-Fi
wifi.interface=wlan0
end of device/oneplus/msm8998-common/system.prop
ADDITIONAL_BUILD_PROPERTIES
ro.treble.enabled=true
persist.debug.dalvik.vm.core_platform_api_policy=just-warn
dalvik.vm.lockprof.threshold=500
net.bt.name=Android
ro.build.fingerprint=OnePlus/OnePlus5/OnePlus5:10/QKQ1.191014.012/2010292059:user/release-keys
ro.lineige.version=0.22-r-20220224165877-release-cheeseburger
ro.lineige.releasetype=dev
ro.lineige.build.version=0.22
ro.modversion=0.22-r-20220224165877-dev-cheeseburger
ro.lineigelegal.url=https://lineigeos.org/legal
ro.elegal.url=https://e.foundation/legal
ro.cm.build.pipeline.id=165877
ro.cm.build.pipeline.iid=7199
ro.lineige.display.version=0.22-20220224165877
ro.lineige.build.version.plat.sdk=9
All this I have been changing it in my computer so I get the new build, which I sideload it to my device.
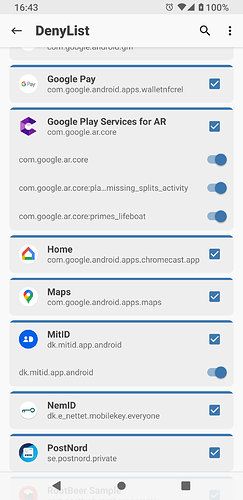
Then I have install magisk, do all what you have write, but I am not sure what to put in deny list. I have put there mitID and Aurora Store and microG. Mitid has been installed from Aurora Store.
And still the phone is recognize like rooted
![]()