I strongly discourage you guys from solely using the host file to block websites, especially when you are doing this on your computer.
This has several reasons:
-
It’s not mandatory for browsers to use the system’s host file. Incase you have a misconfiguration, a file with a false extension or the program simply bypasses the OS resolver, the host file will be ignored. If you do not notice that, you will be fully exposed to tracking.
-
Following scenario: You visit the site ‘test.com’ by typing the address in your browser’s search bar. The webserver internally redirects you to ‘www.test.com’ as this is the common hostname used by the website. If you now block the site ‘test.com’ by adding an entry to your host file, you can’t be sure that it is actually blocked as your browser eventually has already cached the redirect to ‘www.test.com’ and will now connect you directly. Therefore connections are still possible although you allegedly blocked the hostname (but not the www. one).
-
Things may change with future updates. Who knows, maybe browser manufacturers will start to ignore the host file by default, especially when DoH is introduced more and more?
-
The host file has no use if you are using DoT/DoH in your browser as the local OS resolving is bypassed (which is the whole point of DoH). This is especially dangerous for Firefox users as Mozilla started to enabled DoH by default this year (not yet for all users as far as I know). If you are not aware of this, then suddenly also all your ad-blocking will be gone and all counter measures taken (Pi hole, etc.) are worthless as all DNS queries are encrypted (which generally is a good thing for privacy outside your network but not security). Android 9 also introduced DoT, so apps who connect to tracking services over DoT won’t be stopped by your host file.
As you should notice at this point, there are many things that can possibly go wrong and it’s so easy to have your data leaked here. I would always recommend you to block tracking websites as soon as possible which is in the browser directly (for example with uBlock,etc.). This is probably the safest variant with the least potential for data leaks.
A good solution for Android is the app NetGuard. It also relies on the system’s host file but acts like a local VPN. Therefore, all requests made have to be routed through the VPN interface which allows the app to gain full device-wide controll over all connections and decide on its own again wether the request should be allowed or forbidden.
Edit: I’m not sure though how NetGuard handles DoT connections on Android 9 and upwards. I don’t think that it can block those requests. So I would assume that you actually have to locally resolve those queries again. I haven’t made any research here as I’m still on Android 8, would be nice to know if somebody knows ![]()
If you are still looking for an OS-wide solution while maintaining privacy through DoH, I’d recommend you to use a local proxy like Stubby (https://github.com/getdnsapi/stubby) or dnscrypt-proxy (https://github.com/DNSCrypt/dnscrypt-proxy). Stubby is simply a local DNS resolver which accepts unencrypted DNS requests, encrypts them and then connects to a DoH server to read the IP address. So you have to do some adblocking before, either with firewall rules or another proxy.
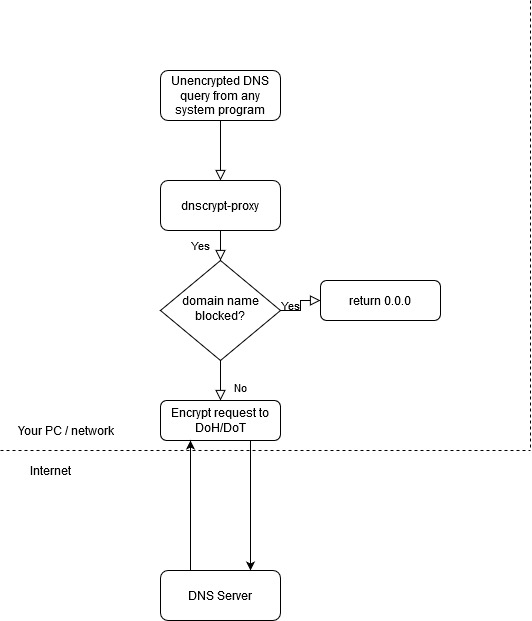
Dnscrypt-proxy already features ad blocking so that’s maybe easier to set up. You could just feed the proxy your hostfile which will then block all malicious/ad-related domains before encrypting to DoH.
So with dnscrypt-proxy your data flow would look something like this:
Another tip for hostfiles: I’d recommend you to create your hostfiles depending on ASNs. If you visit this site here, you will get all IPs for the ASN 15169 which is Google LLC. That’s a good way to quickly block whole providers.