Continuing the discussion I started here. I think this warrants a separate thread.
In short, I noticed that the list of trackers caught by Advanced Privacy for an app diverges from that from Exodus, as listed in App Lounge. Genereally, the list in Advanced Privacy is quite a bit shorter.
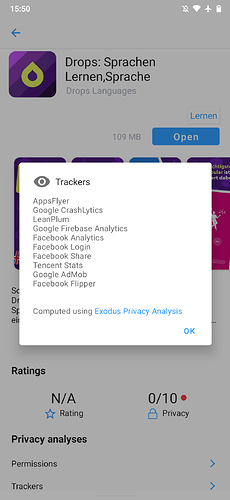
My first test subject was the Drops language learning app, which is infested with quite a few trackers.
This is the list of trackers as listed by Exodus Privacy via App Lounge:
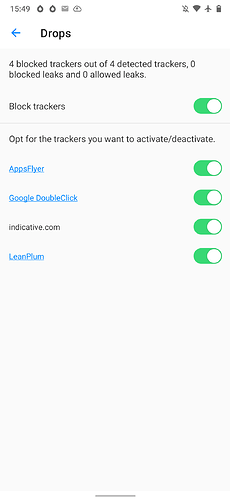
This is the list of trackers as caught by Advanced Privacy:
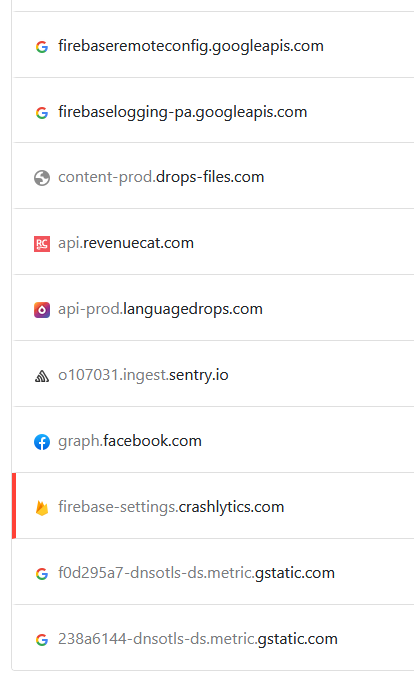
@tcecyk kindly suggested to use NextDNS as a tool for further investigation, which was a great tip. Here are the results of opening the app:
We can draw the following conclusions:
-
/e/ seems to report changes to the DNS settings to a Google domain that looks a lot like an analytics endpoint to me (the two connections on the bottom of the list). Unless this is somehow NextDNS using Google infrastructure to provide its services, this is bad and should be fixed.
-
The trackers that are caught by Advanced Privacy, such as Lean Plum, are not in the list of DNS queries. It stands to reason that the DNS queries for these get filtered by Advanced Privacy. In other words, what ultimately does end up in the NextDNS log are likely tracking connections that actually leak data.
-
Some trackers from the Exodus list are conspicuously absent from both AP and NextDNS. This means they are either false alarms, contacted directly based on an IP anddress instead of a domain or only get activated under certain conditions (say, Tencent Analytics might only get activated when the user has a Chinese IP to avoid scrutiny). This needs some further investigation.
-
Tracking information is likely being leaked to five different services by four different companies (Google with Firebase Logs/Crashlytics, Facebook, Revenuecat, Sentry.io) despite Advanced Privacy being active. All of these domains can be blocked without adverse effects on the functionality of the app.
I have checked the block list used internally by Advanced Privacy that @tcecyk pointed me to. Despite some of those endpoints being among the most common tracking domains (virtually every Play Store app connects to them), they are somehow omitted from the list of known trackers. facebook.net is another one, though it is not contacted in this example.
Given these results, as great as it is in principle, Advanced Privacy seems to give users a false sense of security at this stage.
For now, can anybody tell me where that e_trackers.json file is located on the device so I can adb push an edited version to my device for further research and testing? Is there maybe an additional JSON file where user entries can be added, so it won’t be overwritten by an update? If that’s not possible, I’ll probably replace AP with a firewall app as a workaround for now as right now, I’m not quite ready to mess with custom builds and flashing them onto a production system.