In the last couple of years, words like Data privacy and data piracy are making more and more the headlines. Private corporations and government agencies are actively snooping in our daily lives to know everything about us. Big tech and other corporations have flourished abusing and selling user data to the best offering.
Our smartphones, our daily companions, have become the best device to track us 24/7 as they know with precision where we are, with whom we communicate, what are we doing at any given time, etc… The combination of a handheld computer with a GPS, a camera and a microphone has created a great tracking device we keep next to use at all times.
If you think we are making this up to scare you, read on. In a new study led by the Trinity College of Dublin and the University of Edinburgh, researchers have confirmed in detail the massive amount of user personal data captured by standard smartphones at the operating system level.
So far many studies had focused on the massive data collection from apps, but none had really deep dive into leaks at the operating system level.
The study reveals that Samsung, Xiaomi, Huawei and Realme Android variants all transmit a huge amount of data to the OS developer (i.e. Samsung etc) but also to third-party parties that have pre-installed system apps (including Google, Microsoft, LinkedIn, Facebook). Even the most privacy-conscious users, unchecking options to share data and only following mandatory terms and conditions, will not be safe with those variants.
Thankfully, researchers confirmed that there are options to escape this massive data extraction. We were proud to read their confirmation that “/e/OS collects essentially no data and in that sense is by far the most private of the Android OS variants studied.”
What do we speak about when we refer to data collection via the Operating System?
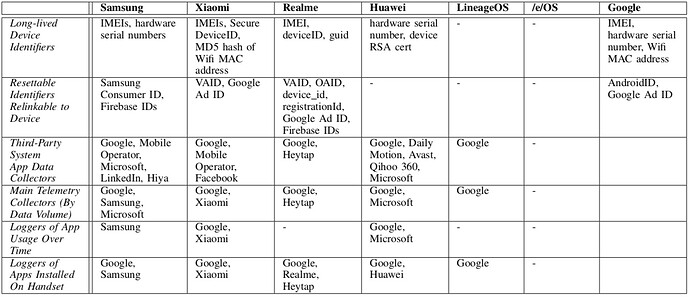
This data collection is the Operating System can be articulated in 3 main areas as pictured in Figure 1:
- the phone unique identifiers like the IMEI, the phone serial number…
- the list of apps installed on your phone
- the interactions with the phone
Summary of data collection by each Android OS variant tested
The phone unique identifiers
Every mobile phone comes with a set of unique identifiers to be able to isolate it from any other phone. There are several identifiers with every phone:
1- The IMEI or International Mobile Equipment Identity is a unique 15-digit code that uniquely identifies each GSM, UMTS or LTE mobile phone terminal. It is the combination of the phone brand, the phone model and variant. This identifier is normally not resettable.
2- The SIM IMSI or International Mobile Subscriber Identifier is another unique number that identifies your SIM card within your mobile network operator. It is basically the combination of your region, your carrier and your mobile subscription number.can help knowing the region and the carrier you are using. This number enables network operators use to identify a subscriber. This identifier is normally not resettable.
3- The hardware serial number which is a unique number identifying the hardware at the manufacturer. This identifier is normally not resettable.
4- The Google Advertising ID which a unique identifier that Google and advertisers or developers use to connect a profile with target advertising based on the user habits. This identifier is now resettable to supposedly enable any user to escape from microtargeting
These are not the only identifiers to fingerprint a user but they are the most common.
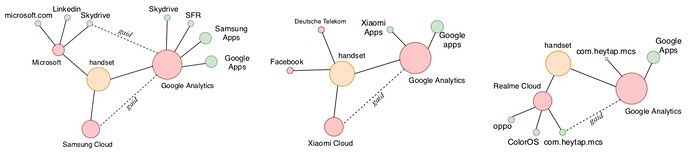
The study found in most cases, all those long lived identifiers (1, 2 and 3) are sent next to the user resettable identifier like the Google advertising ID, meaning that when a user resets is advertising profile, it doesn’t take long before this user will be re-linked back to the same device and an existing advertising profile.
Visualization of cross-linking data collection with different handsets
Except for /e/OS, most of the Android variants tested in the study also collect advertising identifiers and contribute to this cross-linking and endless tracking.
The list of apps installed on the phone
The study found that Samsung, Xiaomi, Realme, Huawei and Google are collecting details of installed apps on each device. While it doesn’t seem that much of an issue to allow those companies to know that you have installed Whatsapp or Uber on your phone, it might be a different story once you install apps that can link you to a specific religious community, political activism, specific gender communities, etc… Especially as these listings can be combined with the phone identifiers to narrow down with precision who you are.
It doesn’t take long for a data broker to access these information and sell to governments agencies like highlighted in this article by Vice Media
The interactions with the phone (Telemetry)
Aside from /e/OS and LineageOS, all systems tested in this study log user interaction, including screens / activities viewed plus duration and time stamp, and logs the event that text is sent.
In some cases, researchers observed that default apps like LinkedIn, installed as a system app, also send telemetry to LinkedIn servers even despite no Microsoft or LinkedIn app was ever opened on the phone, and no request to send the data was observed.
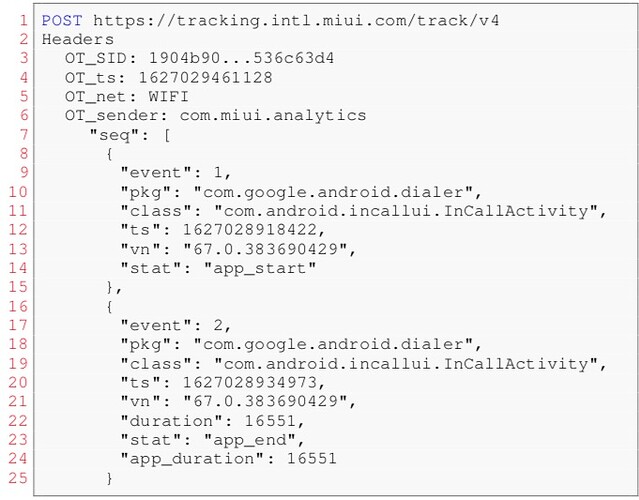
The study also found that some manufacturers like Xiaomi collective extensive telemetry even of your phone calls, logging with precision when the phone calls starts and ends.
Telemetry logs captured by Xiaomi when using phone dialer app
This telemetry is then shared and stored all over the world as the researchers discovered: in Europe mainly in this case but also in Singapore and in the USA,
On every handset, apart from the /e/OS handset, Google collects a significant volume of data. The study highlights that the amount of data collected by Google can be up 10x that uploaded by the mobile OS developer. For manufacturers like Xiaomi, Huawei and Realme the volume rises to around 30x. All this data is captured despite “usage & diagnostics” options being disabled for Google services on all handsets.
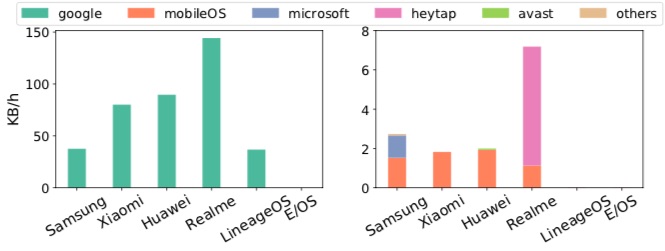
Average volume of network traffic generated on each handset by data collector
We are pleased with the results of this study as validate our claims and ambition by showing that /e/OS captures doesn’t capture any data at all, no identifiers, no list of apps, no user telemetry.
While this study didn’t focus on all solutions available out there, like Graphene or CalyxOS, it is clear that aside from /e/OS, there is hardly any escape from this massive data collection with common phones.
How do we do it differently in /e/OS?
/e/OS isn’t just an Android version with no Google Services Installed. We go much beyond removing from the Android core all pieces of code that phone home to Google without the user active consent.
Compared to other Android variants, even the bare AOSP, we don’t use Google servers to check connectivity upon start-up, we don’t use Google NTP (Network Time Protocol) servers, we don’t use Google DNS (Domain Name System) default servers, and we don’t rely on Google geolocation services. This is also to ensure that your personal identifiers like your IMEI or phone number aren’t collected by simple requests without your consent. We want to ensure your data is safe all the way.
/e/OS is now available on 190 different phones. We keep adding newer device’s to /e/OS every week and upgrading existing ones too. The goal is to enable a large majority of people to escape from this massive data collection imposed onto them.
/e/OS can be downloaded for compatible phones free from the documentation site.
Phones with /e/OS pre-installed are available to purchase from the online shop.
The complete study, Android Mobile OS Snooping By Samsung, Xiaomi, Huawei and Realme Handsets, is available at this URL:
https://www.scss.tcd.ie/Doug.Leith/Android_privacy_report.pdf
Where can you help?
We are always looking for human and financial support to keep innovating and develop this alternative that is more than ever essential to safeguard one of our fundamental rights, privacy.
You can support /e/OS in many ways:
- Join our tribe and install /e/OS on your phone
- Purchase a phone with /e/OS pre-installed from our shop
- Join our community
- Check job openings
- Contribute financially
And spread the word to friends, family, colleagues!
“Your data is YOUR data”
Regain your privacy! Adopt /e/ the unGoogled mobile OS and online services