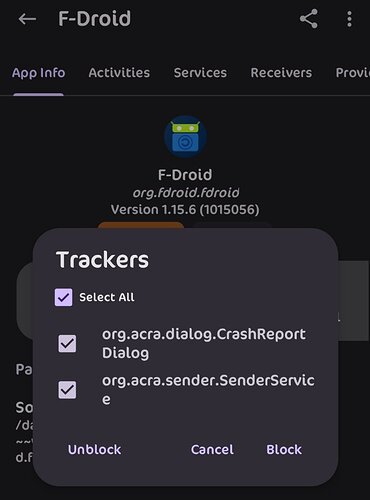
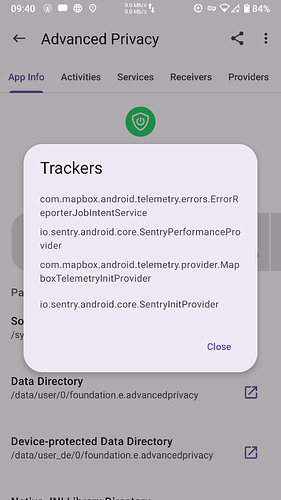
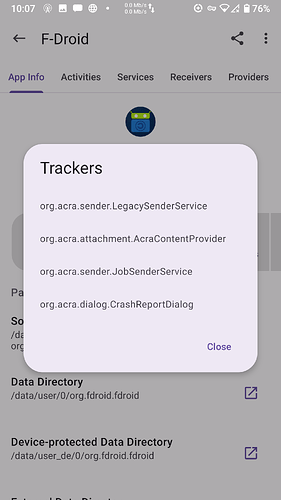
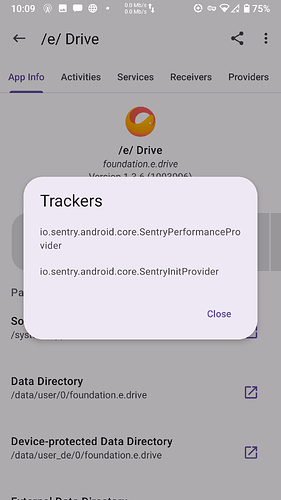
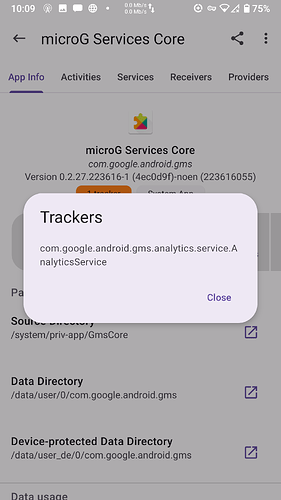
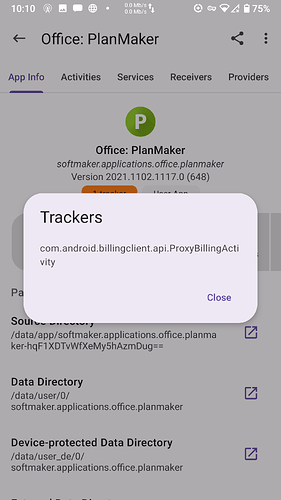
I believe App Manager actually scans the apps themselves. Getting info from their libraries, blobs, and whatnot. So what it finds is actual. Sort of. Categorized by providers, services, activities, and receivers.
In the past, App Manager used to use Exodus for tracker info before scanner improvements.
I did a little write-up in these forums about blocking trackers with AM but that was back in the v2.x days. Things have gotten easier/better since then.
Among App Manager’s features is it can be used to install apps and is recognized by Aurora Store as an installation method (AM Installer). AM Installer can be set to block all trackers on installation of an app. I use it with Aurora Store or on questionable APKs.
As promised, it is now possible to select splits. AM also provides recommendations based on device configurations. If the app is already installed, recommendations are provided based on the installed app. It is also possible to downgrade to a lower version without data loss if the device has root or ADB. But it should be noted that not all app can be downgraded. Installer is also improved to speed up the installation process, especially, for root users. If the app has already been installed and the new (x)apk(s) is newer or older or the same version with a different signature, AM will display a list of changes similar to What’s New before prompting the user to install the app. This is useful if the app has introduced tracker components, new permissions, etc.
Application installer includes several improvements including the ability to downgrade applications in no-root mode, installing multiple applications at once and blocking trackers after installation. In Android 12 and later, no-root users can update applications without any user interactions.
Of course blocking all trackers may cause an issue for some apps but necessary trackers can be unblocked. Mentioned in its documentation.
Never really checked out its documentation much until now. For trackers it states…
Tracker — Denotes tracker components throughout the document and in App Manager except in the scanner page. Trackers include libraries such as crash reporters, analytics, profiling, identification, ad, location, etc. Thus, they are not equal in functions. There is no distinction or bias between open source and closed source libraries that promote tracking.
and
Disclaimer.
App Manager only scans an application statically without prejudice. The application may provide the options for opting out, or in some cases, certain features of the tracker may not be used at all by the application (e.g. F-Droid), or some applications may simply use them as placeholders to prevent the breaking of certain features (e.g. Fennec F-Droid). The intention of the scanner is to give you an idea about what the APK might contain. It should be taken as an initial step for further investigations.
I’ve seen some folks online who don’t want trackers of any kind, good or bad. Being able to see all gives them the ability to block them.
The app works best when rooted but can also use ADB over TCP and Wireless debugging. Never tried either.
App Manager - Android package manager | F-Droid
Latest v3.1.0 is not yet on F-Droid.