Hi @marcdw pl can you raise it as a request on Gitlab. Will label it a feature request. This would be a nice feature to have on the /e/OS
This is a fine variation and would also be a unique selling point for /e/
Alrighty, I’ll raise a request.
Had to do some checking so I could at least provide something for the devs to look at.
Just guessing here, the microG folks provide signature spoofing patches for the various Android versions. Will assume those are what’s used by LOS_microG and /e/ (before any hardening or whatnot).
There are those already working on extending the patches to add the features I mentioned. I’ll look around for others but at least I have a couple to use in the request.
I have tried the apply the patch from here, but build fails:
frameworks/base/core/res/AndroidManifest.xml:2362: error: resource string/permdesc_fakePackageSignature (aka android:string/permdesc_fakePackageSignature) not found.
frameworks/base/core/res/AndroidManifest.xml:2362: error: resource string/permlab_fakePackageSignature (aka android:string/permlab_fakePackageSignature) not found.
frameworks/base/core/res/AndroidManifest.xml:2369: error: resource string/permdesc_fakePackageSignature (aka android:string/permdesc_fakePackageSignature) not found.
frameworks/base/core/res/AndroidManifest.xml:2369: error: resource string/permlab_fakePackageSignature (aka android:string/permlab_fakePackageSignature) not found.
Don’t know and nothing found about this ‘fakePackageSignature’
“That’s because the signature spoofing is set to restricted, meaning it’s only available for system privileged apps, and not user apps.”
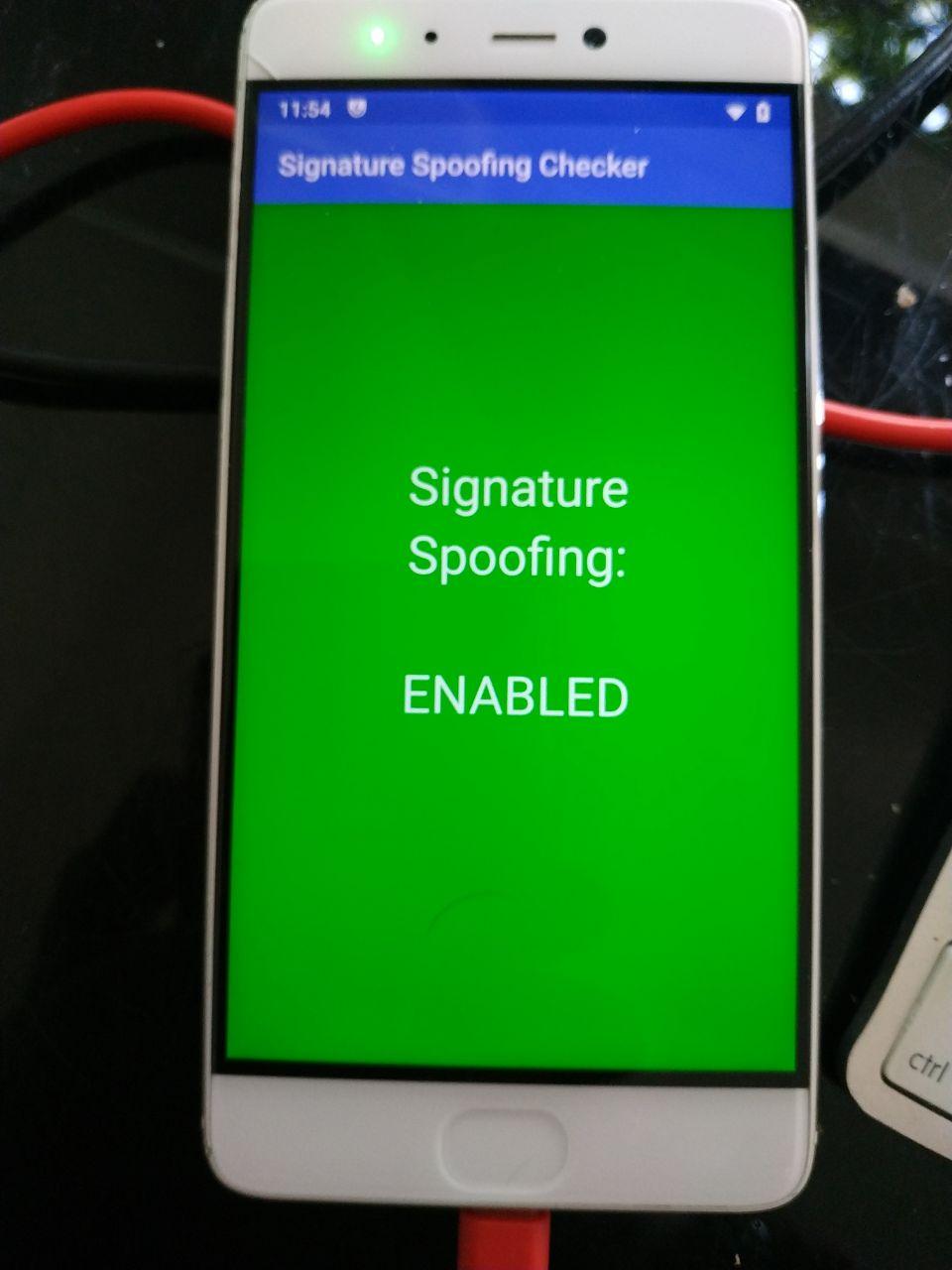
Good to know. I was wondering why the app shows “Signature Spoofing: DISABLED”. In that case it’s generally like that on e. If someone wants to know what it is all about, here are some details:
https://blogs.fsfe.org/larma/2016/microg-signature-spoofing-security/
 Geht doch! Gut gemacht.
Geht doch! Gut gemacht. 
Geht nich, gibt’s nich 
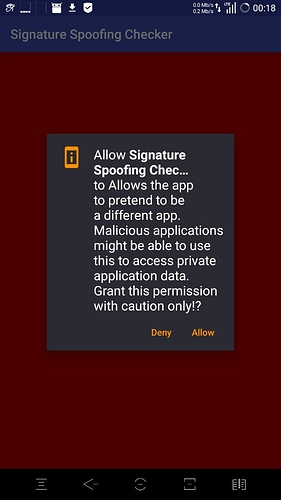
The signature spoofing is not available for user apps, only system apps. So don’t worry about signature spoofing.
And again, if you don’t want MicroG, disable it. It’s easy.
this signature spoofing enabled screenshot I only get with my modifications. On ‘normal’ eOS it allways showing the red screen with spoofing disabled.
I’m nit sure how this signature spoofing is working and do we really need it. But a lot of people asking for it
Hej @Andy, this is about something very different than your microG /e/ trauma.
I’m also tired of you hijacking other topics for “your th/e/ma” here in the /e/ forum and distorting them with repeating endless phrases. I only skim your postings and don’t read them completely anymore. What you are doing here I do not like at all.
I’m happy about the success of @harvey186 posting #26 and the idea of @marcdw posting #20.
Feel free to use the “Ignored” feature of the forum.
You ask him not to talk about that here, but you reply to him here instead of “internal or external mail”. Try to show the example.
Let’s go back to the topic ![]()
To add to what @Anonyme mentioned earlier, the LineageOS for microG FAQ mentions the following…
The signature spoofing could be an unsafe feature only if the user blindly gives any permission to any app, as this permission can’t be obtained automatically by the apps.
Moreover, to further strengthen the security of our ROM, we modified the signature spoofing permission so that only system privileged apps can obtain it, and no security threat is posed to our users.
I always assumed that /e/ was based on LOS_microG. If it is (or not) I also assume its signature spoofing is secured in the same way. Negative result from Signature Spoofing Checker leads me to believe it is. Good.
Now I have to question the others. I run (multi boot) a bunch of ROMs, mostly with sigspoofing and microG. The Checker will let me know if they’re as locked down as /e/ or more open. Normally, one still has to explicitly grant permission to apps to use the spoofing. Over time I have found a few user apps that have had permissions explicitly granted that were outside the normal App Permissions toggles (for things not related to this topic).
It wouldn’t be farfetched to think that couldn’t happen with a less-than-secure signature spoofing implementation.
I have never read of any issues/problems/exploits regarding this stuff. So far so good.
I’m completely overwhelmed with the subject.
I always thought that signature spoofing is there to check if the apk is ‘untouched’. So it wasn’t veined by a stranger.
If this is is, then it’s OK if the user apps have this access to spoofing. Why is it ‘unsafe’ then?
Do I get the whole signature spoofing thing wrong ?
I’ll admit I don’t know a lot about the subject. This article from several years back explains things pretty well I think.
microG Signature Spoofing and its Security Implications
EDIT: Includes info on why Cyanogenmod/Lineage won’t use it.
@Andy1, oh, sorry about that. The LOS_microG was me being too lazy to type out LineageOS for microG.
I now see how that may appear to be something else. 
To add more noise to the topic. Decided to see what Signature Spoofing Checker reports on various setups.
Let’s say, for the sake of argument, there are four levels of signature spoofing support.
Level 1: Built in, used by system(?) privileged apps only. /e/OS and LineageOS for microG. Checker will return DISABLED since it is not privileged and cannot access.
Level 2: Built in, permissions based. Apps need to be granted permission first. Checker will prompt. If denied it will show DISABLED.
Level 3: User patched. Resurrection Remix Nougat patched with NanoDroid-patcher. Checker returns ENABLED. No prompts, no added security.
Level 4: Xposed FakeGApps. Old Samsung Galaxy Light with CM12 and microG. Checker shows DISABLED. Not sure if that means FakeGApps only works with selected apps or if the checker doesn’t know to consult the module.
If one had to worry, level 3 would be the one. For the worry warts. ![]()
Level 2 is what I’, also getting on my eOS.
And I’m still not sure what is the best. Would be fine if a dev could tell us more
I second the motion of @archje. From the standpoint of maximizing your privacy, /e/ without MicroG is better than /e/ with MicroG.
I see some variation here, which also has appeal to me. How about /e/ without MicroG and the signature spoofing present but default disabled? Then, if someone really wants it, he (or I) has to tap somewhere 7 times? Create a hurdle towards lowering the privacy safety? Personally I have disabled MicroG, but when I in the future would assist someone else (‘mom and dad’?) in the use of his/her /e/ phone, I would like to have some certainty that with non-technical users the device stays safe maximally.
Basicly, what you are suggesting is something I think is already available. You can install LineageOS without any Google componant (don’t install GApps, OpenGApps, BitGApps or MicroG). It doesn’t have the /e/ suite of apps, but it has a host of other apps that are open source and has no Google reference.
Isn’t this what you want? Hoping I can be helpful with this. Have a great day.