Recently I had been setting up a couple of ROMs on my Motos (potter Nougat and Sanders Oreo) to be a bit more private and fairly minimal (UnifiedNlp instead of microG, Simple Mobile Tools as default apps on one ROM - at the system level, mostly FOSS only apps, etc.). TrackerControl (TC) of course for its intended purpose as well as a simple on/off firewall to keep some apps from accessing the net.
I’ve had Tor Browser on several ROMs but realized I didn’t make much use of it. Installed Orbot instead and configured various browsers to use it. Never used it as a VPN because I didn’t want to give up TC. So, kind of limited really.
I have a new phone with Android 11. Not rooted or unlocked (not possible yet) so can’t be debloated. Disabled almost everything Google possible and use stuff from F-Droid.
Was going to use Orbot on it but decided to try InviZible Pro instead. Has Tor, DNSCrypt, and I2P. Works as root, VPN, or proxy. Using it as VPN at the moment. All good.
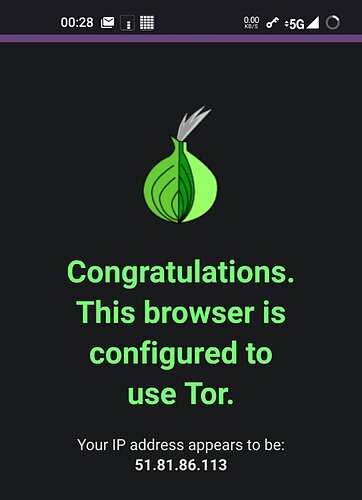
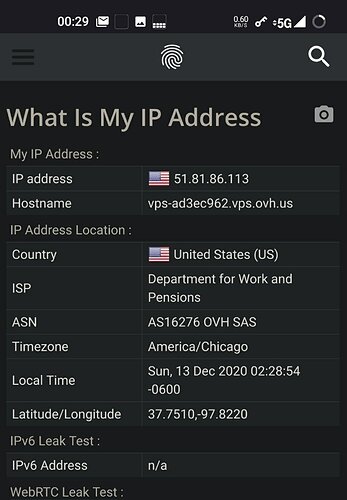
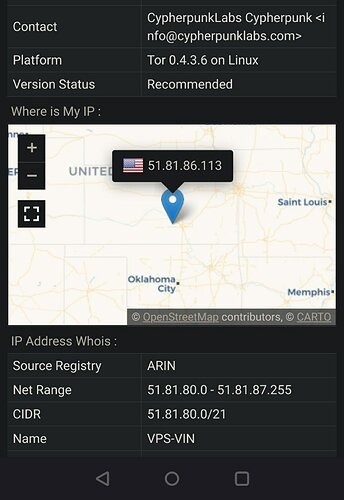
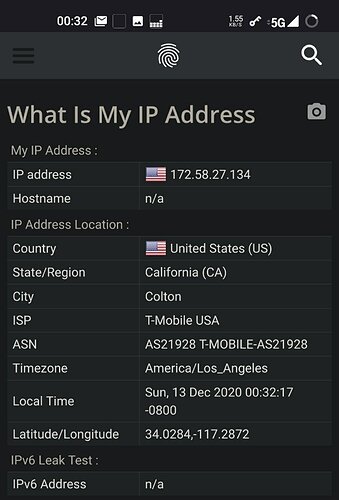
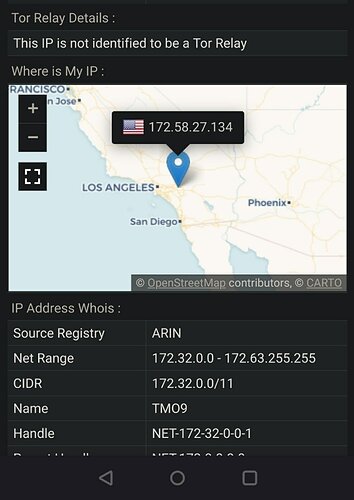
So I went with InviZible on the Motos. Root mode. Definitely works. All browsers show they’re using Tor without any or minimal changes. I’m in Los Angeles County, California, USA. Browserleaks site shows the T-Mobile addresses and map to be local. After enabling InviZible I’m now in Finland, Germany, France, what have you. Good.
Then I got hit by a years old snag. Cannot retrieve MMS.
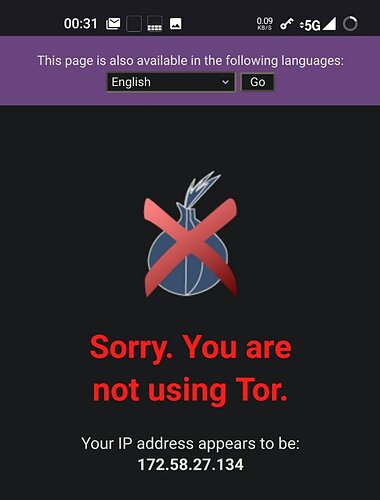
I was going through all kinds of means to get that to work to no avail. Consult the logs, whitelist any domains used for retrieving MMS plus excluding the messaging app plus any system app I thought was related. Still a no go. Turn off InviZible (and Orbot when testing that) and then the MMS immediately downloaded.
Bummer, I thought. Was about to uninstall before I checked out the InviZible help page InviZible and NetGuard firewall. Given TC’s lineage and recent addition of port forwarding, maybe I can apply that.
Yep, that was the ticket. Use InviZible Pro in proxy mode, setup TC as per NetGuard (only minor differences) and it becomes a simple frontend. All traffic is still routed through Tor and I suppose DNScrypt is used.
Normally I have all browsers excluded in TrackerControl (even the Dev recommended that) but for this I enabled all monitoring before testing.
Now here is where the TC part shines. Still can’t get MMS but all I had to do, in TC, was turn off monitoring for my messaging app. Boom, immediately the MMS came in. Simple. No need to mess around inside of InviZible to exclude apps or whitelist domains when one can easily toggle from within TC.
On another ROM where I still have RoboForm, I couldn’t access my credit card site. Flip a switch in TC and all was good.
TrackerControl becomes the easy tool for managing which apps send their traffic through Tor.
Oddly, on the Android 11 device using InviZible, OnePlus 8T w/OxygenOS 11, it doesn’t have any issues receiving MMS. It uses Silence as the messaging app. 
Notes: InviZible Pro via the Play Store is version 5.0.0 and does NOT include adblocking (DNSCrypt?). That version is also in the /e/ Apps store. Probably not an issue if TrackerControl is being used.
F-Droid version (via IzzyOnDroid repo) is version 1.1.5 (November 2020). Also available direct from InviZible.net.
Edit: Many thanks to @harvey186 who pretty much showed us the way with TrackerControl back when. I dumped my regular VPNs and haven’t looked back. It just gets better.