As already written in another thread, I was quite curious about /e/OS 2.6 as it potentially opens the door to using passkeys. So, I (partially ![]() ) spent my Christmas holidays playing around with the new features and want to give an update.
) spent my Christmas holidays playing around with the new features and want to give an update.
First of all, what changed with /e/OS 2.6:
- Switch to microG
v0.3.2.240913-102, i.e. FIDO2 USB-C sticks with PINs should now be supported - Switch to Android
v14, i.e. the underlying OS now supports 3rd party passkey providers.
FIDO2 USB-C stick
Unfortunately, option #1 does not work: my FIDO2 USB-C contains a passkey for github.com. When I plug this stick into my FP4 and try to log in on github.com on any major browser (Firefox, Chrome, Edge), nothing happens.
While this was a bit disappointing in the first place, it’s not such a big deal since having a dedicated USB device that I always have to carry with me wasn’t my favorite option anyway.
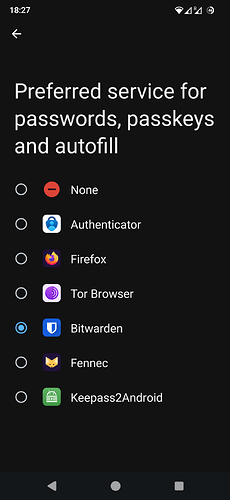
3rd party passkey providers
I have a Raspberry Pi, so could easily run a Docker Compose stack of the Bitwarden Unified Deployment beta. This took a bit of time due to my network settings at home (reverse proxy, custom Public Key Infrastructure, etc.), but the process was straightforward and rather easy. After an hour or so, I had an up-and-running Bitwarden instance and could connect to it using my Win11 machine. Next, I installed the Bitwarden add-on for Firefox and created a passkey for github.com without any issues.
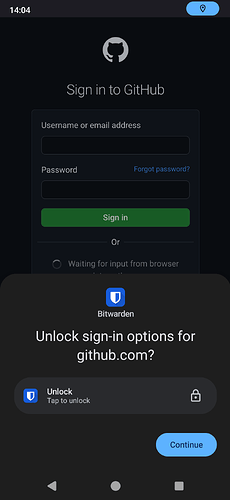
Now comes the interesting piece: I’ve installed the Bitwarden Android app on my FP4 and could connect to the self-hosted Bitwarden server running on my Raspi without any issues. When navigating to github.com in Firefox for Android, I could successfully use the previously created passkey to login ![]()
![]()
This setting is now up and running for almost two weeks and several created and used passkeys later, I must admit that I’m more than happy. There are some glitches here and there (e.g. Bitwarden Docker container still runs as root, no distroless Docker image yet), but the main purpose of providing me with a reliable passkey platform works like a charm.
Don’t hesitate to ask any questions ![]()