Hi,
I just got my Fairphone 3 (after my refurbished /e/ Samsung Galaxy S7 Edge), but Snoopsnitch is failing to produce the report on both of them.
Is it a known issue?
Regain your privacy! Adopt /e/ the unGoogled mobile OS and online services
Hi,
I just got my Fairphone 3 (after my refurbished /e/ Samsung Galaxy S7 Edge), but Snoopsnitch is failing to produce the report on both of them.
Is it a known issue?
Regain your privacy! Adopt /e/ the unGoogled mobile OS and online services
I have just tried on my MiMax3 with eOS pie GSI and it’s working. Have you running any firewall or blokada or something else?
Which kind of registered account do you have on your device?
On my side I only have a nextcloud one.
I tried it on IMG-e-0.10-p-2020080666687-dev-FP3.zip, without anything particular in configuration (no firewall, no Blokada).
Does it have any impact of snoopsnitch ?
I have only my own nextcloud server account added
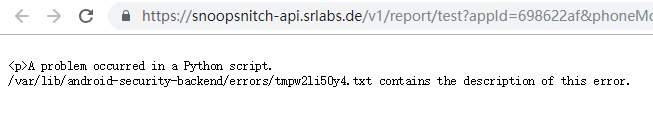
It was my guess, but it seems this is not the case ![]()
I just launched it again, tracking the logs.
There are at least 2 bad things ![]()
08-18 10:10:13.222 22685 22719 E PatchAnalysis: Exception while downloading and parsing basic test chunk: https://snoopsnitch-api.srlabs.de/chunks/ed323a843734d4fdaf7d7b79b5ff45941b6bbb8534c558c92c3f2dadc380af77.json
08-18 10:10:13.222 22685 22719 E PatchAnalysis: java.lang.IllegalStateException: Unknown testType of basicTest
08-18 10:10:13.222 22685 22719 E PatchAnalysis: at de.srlabs.patchanalysis_module.util.BasicTestParser.checkTestTypeSufficientInfo(BasicTestParser.java:317)
08-18 10:10:13.222 22685 22719 E PatchAnalysis: at de.srlabs.patchanalysis_module.helpers.database.DBHelper.insertBasicTestToDB(DBHelper.java:72)
08-18 10:10:13.222 22685 22719 E PatchAnalysis: at de.srlabs.patchanalysis_module.analysis.TestSuite.addBasicTestsToDB(TestSuite.java:60)
08-18 10:10:13.222 22685 22719 E PatchAnalysis: at de.srlabs.patchanalysis_module.analysis.TestSuite.parseBasicTestChunks(TestSuite.java:170)
08-18 10:10:13.222 22685 22719 E PatchAnalysis: at de.srlabs.patchanalysis_module.analysis.TestSuite.parseInfoFromJSON(TestSuite.java:110)
08-18 10:10:13.222 22685 22719 E PatchAnalysis: at de.srlabs.patchanalysis_module.analysis.PatchanalysisService.parseTestSuiteFile(PatchanalysisService.java:156)
08-18 10:10:13.222 22685 22719 E PatchAnalysis: at de.srlabs.patchanalysis_module.analysis.PatchanalysisService.access$1600(PatchanalysisService.java:42)
08-18 10:10:13.222 22685 22719 E PatchAnalysis: at de.srlabs.patchanalysis_module.analysis.PatchanalysisService$DownloadThread.run(PatchanalysisService.java:680)
And:
08-18 10:10:23.036 22685 22743 D PatchAnalysis: number of vulnerabilities to test: 81
08-18 10:10:23.047 22685 22743 E PatchAnalysis: Exception in evaluateVulnerabilitiesTests
08-18 10:10:23.047 22685 22743 E PatchAnalysis: java.lang.NullPointerException: Attempt to invoke virtual method ‘boolean org.json.JSONObject.has(java.lang.String)’ on a null object reference
08-18 10:10:23.047 22685 22743 E PatchAnalysis: at de.srlabs.patchanalysis_module.analysis.BasicTestCache.getOrExecute(BasicTestCache.java:97)
08-18 10:10:23.047 22685 22743 E PatchAnalysis: at de.srlabs.patchanalysis_module.analysis.TestEngine.runTest(TestEngine.java:46)
08-18 10:10:23.047 22685 22743 E PatchAnalysis: at de.srlabs.patchanalysis_module.analysis.TestEngine.runTest(TestEngine.java:64)
08-18 10:10:23.047 22685 22743 E PatchAnalysis: at de.srlabs.patchanalysis_module.analysis.TestEngine.runTest(TestEngine.java:94)
08-18 10:10:23.047 22685 22743 E PatchAnalysis: at de.srlabs.patchanalysis_module.analysis.TestEngine.runTest(TestEngine.java:64)
08-18 10:10:23.047 22685 22743 E PatchAnalysis: at de.srlabs.patchanalysis_module.analysis.PatchanalysisService.evaluateVulnerabilitiesTests(PatchanalysisService.java:262)
08-18 10:10:23.047 22685 22743 E PatchAnalysis: at de.srlabs.patchanalysis_module.analysis.PatchanalysisService.onFinishedAnalysis(PatchanalysisService.java:525)
08-18 10:10:23.047 22685 22743 E PatchAnalysis: at de.srlabs.patchanalysis_module.analysis.PatchanalysisService.updateProgress(PatchanalysisService.java:507)
08-18 10:10:23.047 22685 22743 E PatchAnalysis: at de.srlabs.patchanalysis_module.analysis.ProgressItem.update(ProgressItem.java:17)
08-18 10:10:23.047 22685 22743 E PatchAnalysis: at de.srlabs.patchanalysis_module.analysis.PatchanalysisService$4.run(PatchanalysisService.java:373)
08-18 10:10:23.047 22685 22743 E PatchAnalysis: at de.srlabs.patchanalysis_module.analysis.BasicTestCache$MasterWorkingThread.run(BasicTestCache.java:206)
Do you have any idea?
sorry, no idea 
…
Which version of /e/ os are you using?
Which version of snoopsnitch?
t
The latest version from Aurora
I tried snoop snitch from app store and it does not work no diag access. Does the latest version of snoop still need root access? Where do I get latest version? If I still need root access what is the best way to get it from e OS?
I mannaged to download the latest apk from f-droid, now I need help with root for e OS.
TIA jets
If you will root your device it’s a security violation. So from my side of view, it makes no sense.
Snoop snitch needs root access and I want to run it, so willing to take the risk. Unless you are saying it no longer need root access? But I think that is not the case 
How did you get it running on your phone?
I just installed it from fdroid, it does not work. “Please update to the latest available version”. Fairphone 3 e pre-installed.
Maybe it is due to
Note: Custom Android ROMs like CyanogenMod may or may not work, depending on the availability of a Qualcomm DIAG kernel driver (DIAG_CHAR)
https://f-droid.org/en/packages/de.srlabs.snoopsnitch/
88250,
I was thinking the same thing, but it also say we need root access to the phone. Is your phone rooted?
There is a discussion on rooting the FP3 here https://forum.fairphone.com/t/e-for-fp3-google-free-os/59328/107 The same procedure works with an FP3+. You will have to backup and restore your data to get it to work.
Thanks for the help Bernard, very helpful.
@Bernard yes it is. I had to grant root access when starting.
I have tried to use snoop snitch (2.0.11, 2.0.10 and 2.0.9) to do the patch level analysis without the root access on Huawei Mate20 Pro(Android 10), Xiaomi 10(Android 10), Pixel 2(Android 10), Lenovo (Andorid 7) and Meilan note3(Android 7). But all of the results are failed. I have noticed that the patch level analysis doesn’t need the root access. Did I miss some important configs?
Here is the screenshot:
In addition, here is the logcat:
2020-11-16 20:07:13.958 6052-6398/? E/PatchAnalysis: Exception in evaluateVulnerabilitiesTests
java.lang.NullPointerException: Attempt to invoke virtual method ‘boolean org.json.JSONObject.has(java.lang.String)’ on a null object reference
at de.srlabs.patchanalysis_module.analysis.BasicTestCache.getOrExecute(BasicTestCache.java:97)
at de.srlabs.patchanalysis_module.analysis.TestEngine.runTest(TestEngine.java:46)
at de.srlabs.patchanalysis_module.analysis.TestEngine.runTest(TestEngine.java:64)
at de.srlabs.patchanalysis_module.analysis.TestEngine.runTest(TestEngine.java:94)
at de.srlabs.patchanalysis_module.analysis.PatchanalysisService.evaluateVulnerabilitiesTests(PatchanalysisService.java:262)
at de.srlabs.patchanalysis_module.analysis.PatchanalysisService.onFinishedAnalysis(PatchanalysisService.java:525)
at de.srlabs.patchanalysis_module.analysis.PatchanalysisService.updateProgress(PatchanalysisService.java:507)
at de.srlabs.patchanalysis_module.analysis.ProgressItem.update(ProgressItem.java:17)
at de.srlabs.patchanalysis_module.analysis.PatchanalysisService$4.run(PatchanalysisService.java:373)
at de.srlabs.patchanalysis_module.analysis.BasicTestCache$MasterWorkingThread.run(BasicTestCache.java:206)
From the logcat, I have found that there are two URLs, reportSys() URL and reportTest() URL.
Here is the related logcat:
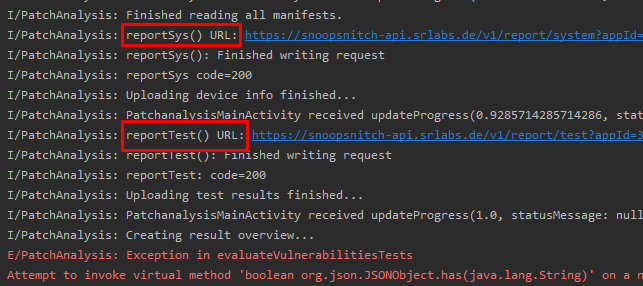
Here is the URL information, which seems like some errors in the server: