Mission:
Learn to encrypt your DNS queries using DNS-over-TLS client implementation known as Private DNS in your smartphone running latest /e/OS.
Prerequisites:
- A smartphone with /e/OS based on Android 9 or newer.
- Patience to fiddle around with /e/OS Settings
Let’s roll.
Why should you Encrypt your DNS?
The same reason why we use https to access our favorite websites including this very forum or wiki. To seek privacy, security and integrity of data communication.
1. Goto /e/OS Settings to open Network & Internet settings therein.

2. In Network & Internet settings, navigate to ‘Advanced’ settings therein
Tap PrivateDNS to continue.
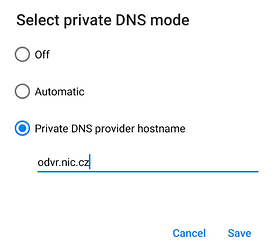
Input a DNS hostname of your choice from various options available across the globe.
Popular public domain name resolving services offering DoT or Private DNS support:
Name | Hostname
Nic.cz | odvr.nic.cz (used in this guide)
Quad9 | dns.quad9.net
Cloudflare | 1dot1dot1dot1.cloudflare-dns.com
Enter DNS hostname of your choice and tap ‘Save’ to continue.
Private DNS attempts to connect when connected you see the hostname in settings as seen in the image below.
3. Check DNS settings or leaks in /e/OS’s browser
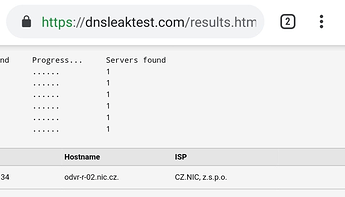
Open https://dnsleaktest.com in /e/OS’s browser and tap Extended test to continue.
Once the test is complete you should exclusively see the DNS servers that you have set in Private DNS settings of your /e/OS, as seen in the image below.
Troubleshooting
If you see the error as seen in the image above, it means you have entered wrong DNS hostname or the service you are using is broke. Try another one to check. It should fix the issue.
Thanks for reading!