Brave is my go to. I haven’t tested may others so I appreciate @marcdw testing and report back here. I posted because I see this as a useful tool that I wanted to make those unaware…aware.
*I have installed InviZable Pro and am a huge fan (I have root via Magisk). Appreciate the suggestion @marcdw. I find it working well with my non-free VPN service. I appreciate the feature in Fast Settings > Start DNSCrypt On Boot (Tor and I2P also listed, not using quite yet). I have my non-free VPN set to run at all times or to “Kill Switch” my data connection. With this set up I know VPN and DNS are masking at all times. Still testing and learning on the Tor and I2P settings.
Another note on App Manager (AM), more testing is needed (comparing directly to Tracker Control) but I am not 100% sure AM is actually blocking trackers in some applications. This, or it is user error on my end. Still needs some testing and will report back.
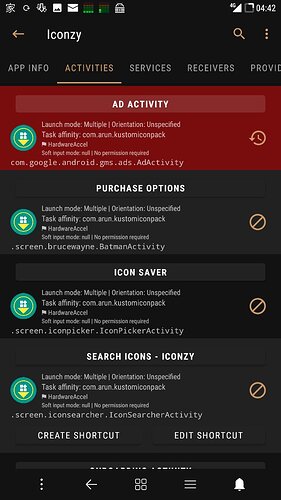
I guess one way to test AM is with apps that have ads. I don’t normally run apps with ads though. Hmm, here’s an example where in-app blocking may be working. On one of my long running ROMs, Bootleggers Oreo, I have an app called Iconzy. I have its ad tracker blocked which causes an error toast to show. When I unblock the tracker the error doesn’t appear. That tells me something is working. Screens below.
But I also don’t see any ads. If there’s supposed to be some kind of ad banner in that area I wonder if something else is blocking them, like AdAway. Will check on that later.
Back before App Manager I used to use MyAndroid Tools to block ads, services, and other things. Definitely worked (most evident when I used to use Tapatalk) but in the years since then the majority of the apps I run are not from the Play Store. Usually I’m blocking app measurement stuff.
Vivaldi showed for me the same result as /e/-browser (blocking everything but unique fingerprint).
Brave’s client-side encrypted sync is what pushed my decision as I use it over a few different devices. Are you aware of any other privacy focused browsers that offer the similar sync capabilities across Android and Linux desktop?
*THIS thread may be of interest to you @chogo browser info discussed
What repository is this found in?
I think I found the .apk if this is it👇 not seeing in FDroid or Aurora… Maybe I missed it. Appreciate the info you share, very helpful in getting me over the learning curve.
Yes, that’s it.
I can honestly say it was THE tool to use awhile back.
Downside might be its age. Last version was 1.6.9 from 2019. Probably targets no higher than Pie. I don’t have anything higher to try it on.
particularly interested in this as well ![]() , XPrivacyLua. Anyone have experience they can share?
, XPrivacyLua. Anyone have experience they can share?
I like App Manager if I have root (need to do some testing with ADB over TCP,) (can’t block trackers without root) if I don’t have root Blokada seems to be a good tool for non-advanced users like me (to get VPN and Tracker blocking together, I want my IP masked and TOR is a bit slow for everyday use via InviZible’s TOR setting).
I have a setup on a phone running Magisk (root), App Manager (tracker blocking root level), InviZible (DNSCrypt), non-free VPN service (Mullvad, Proton, etc.) and it works good but it isn’t a daily driver and I am worried about updates with root (especially on a A/B slot setup).
Because of this I am leaning to go with a non-root setup. I am thinking of utilizing the Android system private DNS (Pihole or NextDNS) with Blokada 5 for VPN and tracker blocking, this runs the gambit I believe. I will also utilize Shelter for the worst apps and sandbox them away from my main profile. (trying to do away with non-FOSS apps, easier said than done).
Am I missing anything on a non-root set up?
*Running private DNS ain’t working with Blokada. It has the same issue as TackerControl, it can’t see the trackers to block/filter.
The more I learn the more it looks like rooting is the only way to get encrypted DNS, VPN, and tracker blocking all working together easily (not utilizing TOR via InviZible).
How difficult is it to not lose root when updating? Any suggestions/places to go for a newb to rooting on how to handle updates easily (especially A/B slots)? I can search but would love for direction from someone wise in this area.
This thead goes into some thoughtful depth.
Sorry to say I won’t be of much help on that topic. My devices are multibooters and run older Androids (KitKat thru Oreo), thus no updates. They also all use SuperSU or Lineage SU (I have never liked Magisk really). I also don’t do OTAs so if a ROM was updated it would be no problem to flash root after flashing ROM.
On my ZTE Axon 7, /e/OS Nougat is the only ROM (of four on the device) that gets updated regularly but it’s been trouble free, from 0.1 to 0.17. I just flash Lineage SU although not really necessary since the addon.d stuff works. Backup and restores have never worked on the Essential for some reason. Even when I was on Nougat.
The one exception is on my Essential Phone with /e/OS Pie running Magisk (the only unlocked device with A/B). Lineage SU wasn’t up to snuff for AdAway, Substratum, or EdXposed. I’m still on Magisk 20.4 there. Any attempt at updating would cause the ROM not to boot. I may try again with version 22.x. Maybe.
One of my pet peeves over the years is how Magisk winds up breaking things after every few updates. Modules breaking with new APIs, out of luck if a favorite module doesn’t get updated to comply (not unlike Xposed modules that don’t get updated when that changes). Root should be simple and just work. But I digress.
An excellent dev by the name of osm0sis on XDA has some tools that may help if you use TWRP and do OTAs on A/B devices. The gist is that it retains TWRP and then one can easily install Magisk afterward. I think.  Never used it before.
Never used it before.
Main thread…
[TOOLS][ZIPS][SCRIPTS] osm0sis’ Odds and Ends [Multiple Devices/Platforms]
TWRP A/B Retention Module script (many devices)
I totally missed your post about non-root set up.
I have one unrooted and locked device, a OnePlus 8T. That one took some experimenting. Also used Mullvad, Psiphon, Proton, etc.
Using the InviZible help guides I settled on the Shadowsocks FOSS with InviZible as VPN. I thought Mullvad would be a good choice but I just couldn’t get it working with Shadowsocks. Probably me not understanding something.
But everything is working great. Using Surfshark with Shadowsocks FOSS, going through InviZible. The Surfshark IP is shown on the outside, while InviZible handles DNSCrypt. I also have Tor and I2P turned on. Speed is not a problem. Browserleaks.com shows that my ISP’s IP is not being used and DNSCrypt is in play.
Note: In Fast Settings I have “Route All traffic through Tor” toggled off. Browsers do their thing normally but can access onion or I2P sites if needed. Apps that have proxy settings (HTTP or SOCKS5), like F-Droid, Aurora Store (before v4.x), EteSync, Nekogram X, etc., are setup to use InviZible for traffic (Tor I guess). All is good.
EDIT: I realized I sort of repeated some things I mentioned earlier. Oops. Might as well repeat one more thing. When InviZible is in VPN mode it also has a firewall. Can be set to notify when a new app is installed whether or not to grant it internet access.
Thank you. Yes some this I read before but it didn’t sync so now I do see additional paths to take/try. Back to the drawing board. Thanks again.
Is there something wrong with this: AdAway (A free and Open Source ad blocker for Android.) - https://f-droid.org/packages/org.adaway
I don’t use it but according to the description it seems to be good.
I use netguard witch is similar.
– Envoyé depuis /e/ Mail.
What are your thoughts of RethinkDNS?
Thanks for sharing. I will read up on this as it is new to me. I did want to post and let others know that the latest version of Blokada does indeed utilize encrypted DNS, a VPN and tracker blocking all in one place without root. It seems this is a good solution for an everyday user (thanks @clame !) where some of the methods provided by @marcdw seem very robust and excellent for power users. Just my 2 cents on what I have learned. Thanks for all the sharing of info here.
No problem. I noticed that some time ago at F-Droid. There’s been some discussion at /e/ public group at telegram and on there one thing related to Blolada came up by then:
https://gitlab.com/fdroid/fdroiddata/-/merge_requests/8536
Reading that through didn’t give so good picture of Blokada devs etc. Sure that issue and fix is raised by RethinkDNS developer, but things didn’t have to go as far they did (especially that F-Droid FUD post, instead just admit mistake and fix it). Blokada could just fix those things after privately was being contacted, if they choose to…
Hmmmm… I have some reading to do. Thank you. There is so much information it is like drinking from a firehose. It would be nice to have a complete privacy related solution for VPN, encrypted DNS and tracker blocking without root. Looking like I may just have to bite the bullet and learn that much more.
I have some reading to do. Thank you. There is so much information it is like drinking from a firehose. It would be nice to have a complete privacy related solution for VPN, encrypted DNS and tracker blocking without root. Looking like I may just have to bite the bullet and learn that much more.
Have used AdAway for years. Before things like Tracker Control I guess my ROMs always had an AdAway/AFWall+ combo. Required root for both.
Starting with AdAway v5 (Oreo and higher only) they added a no-root VPN ad blocker. I’ve never had the chance to use it in that capacity.
On the no-root front there’s also the combo of NetGuard firewall with InviZible Pro as shown here…
InviZible and NetGuard firewall
It was that tutorial I originally used for InviZible with Tracker Control since TC is partially based on NetGuard. Since I was “fresh” at the time I had website issues due to Tor. As mentioned in the article, if Tor is not needed you don’t have to enable the corresponding proxy in NetGuard or TC. So the combo of TC (block trackers) and InviZible (DNSCrypt) is still probably a good deal.
Some notes about InviZible. I originally got it from F-Droid via the IzzyOnDroid repo. Current/latest version is 1.3.3. Same if you get it directly.
It later became available via the normal F-Droid repo. That version is 5.3.0 and corresponds to the Play Store version. Both versions are equal so don’t think one is older or newer than the other. Have no idea why they’re different.
Now, if 32bit vs 64bit is a concern, know this. Both F-Droid offerings are only 32-bit (armeabi). If you want 64bit (arm64) then get InviZible Pro beta directly or (as I did originally with the F-Droid v1.x builds) just update via the app. It will automatically update to 64bit, which most modern phones are.
Last note, in case missed in their respective descriptions, the Play Store versions of Tracker Control and InviZible Pro have some functionality missing. Things that Google won’t allow. I suggest not getting them from Aurora Store.
EDIT: For /e/ Apps store one has to look closely/carefully in figuring out from where something originates. TrackerControl is the F-Droid version so that’s good. For InviZible, there are two versions available, 5.2.1 and 5.3.0. Where does that older version come from? Why is the license unknown?
Better to stick with F-Droid or obtain directly when in doubt.